 Is it possible to "Open With..." another program the currently opened file?
Is it possible to "Open With..." another program the currently opened file?
Currently I'm doing a lot of modifications in CSV files. Sometimes I crave the raw power of ST2, but sometimes I use a dedicated editor, so I switch between both tools a lot.
→ I'd love to have a feature to "Open with ToolXYZ" the currently open file.
Notepad++ has such a feature, you just have to define the tools in the users shortcut.xml, and it looks like this:
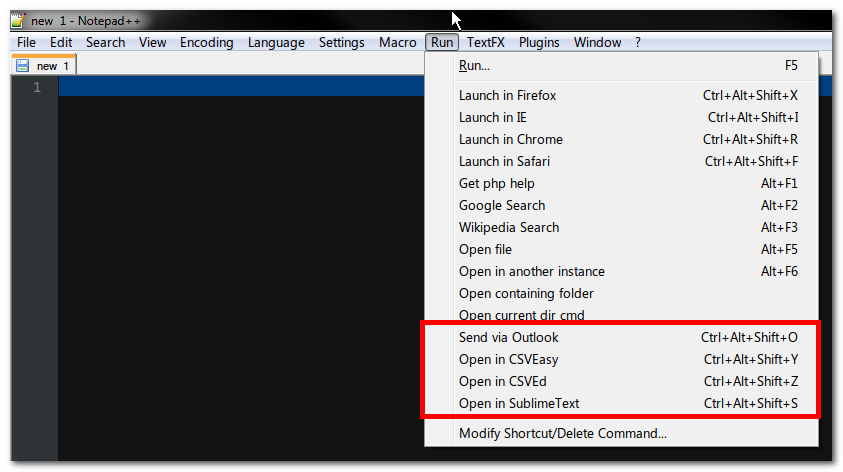
Is it possible to do the same in ST2? Else, the closest plugin I found is sublime-text-2-open-with-vim, that can be easily adapted or generalized. Do you know something closer?

 Westhill Consulting Jakarta What You Need to Know About Ipo Investments
Westhill Consulting Jakarta What You Need to Know About Ipo Investments
Westhill Consulting is a market leader in the Financial Services category. Here is a guide to Initial Public Offerings (IPO's) intended to simplify the jargon and remove the fear that IPO's involve higher risk as compared to usual investments.
Westhill Consulting is a reputable investment advisory firm based in Jakarta Indonesia, dedicated to providing you the most advantageous investments based on how you want your portfolio managed for the private middle market.
You might be wondering how you can increase the profits you make from your market investing strategies. If you're searching for the most profitable forms of investing that are available today, you should definitely investigate the possibilities of using Initial Public Offering (IPO) investments.
A simple description of an IPO includes the fact that you're buying a business that is just entering the open marketplace. The moment the IPO is released to the public is the first time anyone has the ability to buy the company openly, and this will surely give you a good idea on where the stock itself resides when it comes to the value of the offering. You can wage it is preparing for a large rise in its value because they are just releasing their stock to the public.
Though most of the Initial Public Offering stocks skyrocket after they are first released, you must keep in mind that they are hardly a definite investment. Because of this, there are several factors you must definitely examine before you place your capital into this type of investment.
One of the first factors you must take into consideration before investing into the stock you are interested in is the basic fact that once the stock is available on the market you can't guess if there will be a great deal demand or a total lack.
Because of this, you must do your best to ascertain every bit of information available about the company before making a purchase.
As you comb the market for the best IPOs available today, you must consider the fact that IPOs are usually offered only to the market when a company plans on expansion. There are other instances where companies only want to increase their ability to borrow capital, but IPOs are mostly released to increase the amount of funds they have available for expansion plans.
It may look like a company which is preparing to expand is a sure bet on the stock market. However, that is not really the case. IPO stocks are usually considered as high-risk investments. That is why if you want to secure your investments to a degree, you must explore the overall performance of the company's operations in the long run.
When you have analyzed the essentials of the company you are interested on, you must also try to guess where the capital generated from the IPO will be used by the company. If you think the company's only choice is to put their capital into expansion activities, you can be sure that the stock value will increase over time because of the expanding capabilities of the business operation. As you examine the essentials of the company and estimate where the capital will be going once the IPO is sold to the public, you can make a reasonable evaluation of how the stocks are going to fare in the future. Being one of the top advisory firms in the industry, we gain the confidence of our clients by acting with integrity on all our business decisions.
Westhill Consulting practices a specific valuation procedure to determine how much a profitable business is worth and determine possible market opportunities.
http://www.westhillconsulting.com

 Navigate code by hand grab
Navigate code by hand grab
It would be nice to have some feature like hand-grab to navigate code. Just like Gimp, Photoshop, etc.
Sometimes when the code extends so much to the right using scrollbars gets clunky.

 Private Detectives and Investigators
Private Detectives and Investigators
What Private Detectives and Investigators Do
Private detectives and investigators find facts and analyze information about legal, financial, and personal matters. They offer many services, including verifying people's backgrounds, finding missing persons, and investigating computer crimes.
Work Environment
Private detectives and investigators work in many places, depending on the case. Some spend more time in offices doing computer searches, while others spend more time in the field conducting interviews and performing surveillance. They often work irregular hours. About 1 in 5 were self-employed in 2012.
How to Become a Private Detective or Investigator
Private detectives and investigators mostly need several years of work experience in law enforcement. Workers must also have a high school diploma, and the vast majority of states require private detectives and investigators to have a license.
Pay
The median annual wage for private detectives and investigators was $45,740 in May 2012.
Job Outlook
Employment of private detectives and investigators is projected to grow 11 percent from 2012 to 2022, about as fast as the average for all occupations. Demand for private detectives and investigators will stem from security concerns and the need to protect confidential information. Strong competition can be expected for jobs.
Similar Occupations
Compare the job duties, education, job growth, and pay of private detectives and investigators with similar occupations.
More Information, Including Links to O*NET
Learn more about private detectives and investigators by visiting additional resources, including O*NET, a source on key characteristics of workers and occupations.

 Credit Writedowns: Privacy and the ubiquity of embedded technology
Credit Writedowns: Privacy and the ubiquity of embedded technology
Today’s commentary
Yesterday, Google announced that it would buy privately-held Nest Labs for $3.2 billion. This was Google’s second largest acquisition ever. Nest is a smart thermostat and smoke alarm-maker which promises to give Google a leg up in the fast expanding home automation market. But the acquisition also highlights the degree to which communications technology is now embedded in ordinary devices. The benefit is convenience. The risk is privacy.
Since this is a thought piece, I am putting it outside the paywall.
Last week cryptography expert Bruce Schneier wrote an interesting piece on the NSA at the Atlantic, arguing that the intelligence agency threatens national security. His argument in a nutshell was that the NSA – in its zeal to undermine security for espionage purposes - made the digital world vulnerable to any attacker, including foreign governments and common hacker criminals. Schneier pointed to the NSA’s “collect-everything mentality” as being at the heart of the security vulnerability. And I believe this is important when thinking about embedded technology in the context of the Google acquisition.
Embedded technology or embedded systems are computer systems that operate within larger devices in order to make them ‘smart’ and more technologically advanced. Think of electronic watches, baby monitors, refrigerators or washing machines. These articles are by their very nature mechanical/electronic. But in today’s world, they also contain tiny little computers in order to enhance their functionality and ease of use. Embedded systems of this sort are literally ubiquitous. The Nest acquisition gives Google entree into this embedded technology market in its most important application, home automation.
The problem with embedded systems is that they are a major security and privacy risk. In another Bruce Schneier post, he explains:
“We’re at a crisis point now with regard to the security of embedded systems, where computing is embedded into the hardware itself — as with the Internet of Things. These embedded computers are riddled with vulnerabilities, and there’s no good way to patch them.
It’s not unlike what happened in the mid-1990s, when the insecurity of personal computers was reaching crisis levels. Software and operating systems were riddled with security vulnerabilities, and there was no good way to patch them. Companies were trying to keep vulnerabilities secret, and not releasing security updates quickly. And when updates were released, it was hard — if not impossible — to get users to install them. This has changed over the past twenty years, due to a combination of full disclosure — publishing vulnerabilities to force companies to issue patches quicker — and automatic updates: automating the process of installing updates on users’ computers. The results aren’t perfect, but they’re much better than ever before.
But this time the problem is much worse, because the world is different: All of these devices are connected to the Internet. The computers in our routers and modems are much more powerful than the PCs of the mid-1990s, and the Internet of Things will put computers into all sorts of consumer devices. The industries producing these devices are even less capable of fixing the problem than the PC and software industries were.
If we don’t solve this soon, we’re in for a security disaster as hackers figure out that it’s easier to hack routers than computers. At a recent Def Con, a researcher looked at thirty home routers and broke into half of them — including some of the most popular and common brands.”
Schneier focuses on the security risk. And that’s a big problem because these embedded technology products are never updated by end users, making them vulnerable to hackers, especially if they are internet-enabled. But then there is the privacy risk too. A lot of ink has been spilled over GPS and WiFi tracking for example. For retailers, tracking customers in-store will soon be the norm. But these tracking mechanisms can be used across retailers too in the same way tracking cookies are used across the Internet. Turnstyle Solutions has set up a WiFi tracking mechanism in downtown Toronto that uses sensors at 200 different stores, allowing the company to create a mosaic of 2 million people and their shopping habits – in the hopes of serving them with proto-Minority Report-style advertising.
We see the emerging location tracking technology developing in cars too at this year’s Detroit auto show. The Guardian reported on privacy problems:
the US government accountability office (GAO) found inconsistencies in the way automakers handle data from car owners, raising fears of privacy breaches. The study looked at information collected by Chrysler, Ford, General Motors, Honda, Nissan and Toyota as well as navigation device-makers Garmin and TomTom and map and navigation app developers Google and Telenav.
“Without clear disclosures about the purposes, consumers may not be able to effectively judge whether the uses of their location data might violate their privacy,” the report noted.
Now, note, that these technologies are geared not just toward enhancing computing power but toward increasing convenience for end users. So the convenience factor is the trojan horse for security and privacy vulnerabilities. Couldn’t the government embed hidden backdoors into these systems? Couldn’t hackers break into the vendors’ computer systems to access our private information? Couldn’t someone or some company or some government use our home automation devices to watch our every move where we live and sleep? The answer to all of these questions is yes. This is what happened with the Target and Neiman Marcus data breaches, affecting 70 million customers with not just stolen credit card information but stolen email addresses, telephone numbers and other personally identifying information.
I don’t have a solution to this problem but I think it will be end up as a mutli-factored problem in a world that is increasingly dependent on always-on computing and internet communications capabilities. The economic and social impact will be in terms of theft, industrial and government espionage, privacy and freedom of speech. it’s hard to tell when, where and how the privacy and security vulnerabilities will be made manifest as serious problems but the NSA spy scandal tells you it already is one. And it is likely to get bigger unless we do find a solution.
Bruce Schneier makes a good case for seeing the security and privacy risks as social in nature. He writes:
Not only is ubiquitous surveillance ineffective, it is extraordinarily costly. I don’t mean just the budgets, which will continue to skyrocket. Or the diplomatic costs, as country after country learns of our surveillance programs against their citizens. I’m also talking about the cost to our society. It breaks so much of what our society has built. It breaks our political systems, as Congress is unable to provide any meaningfuloversight and citizens are kept in the dark about what government does. It breaks our legal systems, as laws areignoredorreinterpreted, and people are unable to challenge government actions in court. It breaks our commercial systems, as U.S. computer products and services are no longer trusted worldwide. It breaks our technical systems, as the very protocols of the Internet become untrusted. And it breaks our social systems; the loss of privacy, freedom, and liberty is much more damaging to our society than the occasional act of random violence.
And finally, these systems are susceptible to abuse. This is not just a hypothetical problem. Recent history illustrates many episodes where this information was, or would have been, abused: Hoover and his FBI spying, McCarthy, Martin Luther King Jr. and the civil rights movement, anti-war Vietnam protesters, and—more recently—the Occupy movement. Outside the U.S., there are even more extreme examples. Building the surveillance state makes it too easy for people and organizations to slip over the line into abuse.
It’s not just domestic abuse we have to worry about; it’s the rest of the world, too. The more we choose to eavesdrop on the Internet and other communications technologies, the less we are secure from eavesdropping by others.
The end result of not fixing this problem will be an erosion of the legitimacy of government and democracy, something that will eventually create economic upheaval and revolution. One way to hold this at bay is to stop government from exploiting the security and privacy loopholes. But another important factor is for citizens to start taking security and privacy seriously. The trade-off between convenience and privacy/security needs to move more in the direction of security and privacy – and by that I mean we consumers need to force companies to add security into their systems. Two-factor authentication systems and easy to use security protocols. One reason I think Bitcoin is interesting is that it sets up a way for people to interact across the web securely in a way that is independent of the security systems of one individual company. It is the technology behind Bitcoin that provides answers for the future more than the currency, which is a legacy of the increasing distrust of government and the erosion of the legitimacy of democracy.
Eventually, repeated violations of security and the erosion of privacy will lead to a breakdown in society. I think we can have the convenience and the security and the privacy. But we need to take the security and privacy seriously or we won’t get it.

 Layout group resize broke in 2118
Layout group resize broke in 2118
When choosing any layout, except "Single", and trying to drag the grip separating the groups, one of the groups collapses and remains hidden. Specific to SE2 2118

 Improve view.sel() documentation
Improve view.sel() documentation

 Jobs for English teachers in Indonesia Westhill Consulting & Employment
Jobs for English teachers in Indonesia Westhill Consulting & Employment
With a population of approximately 238 million people spread over 17,508 islands along the equator, Indonesia is the world’s fourth most populous country and represents a fast-growing market for English teachers. Those looking to teach English in Indonesia will encounter an entrancing combination of lush, volcanic landscapes; beautiful beaches and thousands of years of history and culture. The country is also known for the warm hospitality of its people, most of whom are Muslim.
English teachers in Indonesia, especially Jakarta, can find teaching jobs year round. Although most interviews are conducted in advance over the phone and via e-mail, some schools prefer to interview in person. Instructors are typically responsible for their own airfare and housing expense, though some schools do provide assistance in these areas. Most live in apartments recently vacated by previous teachers, and many room with coworkers. Watch out for scams in this area.
A generous salary affords English teachers the opportunity to live a comfortable lifestyle, while saving 250–300 USD per month. Schools offer approximately 20 to 25 hours of work per week, leaving plenty of time to travel and explore Indonesia’s exquisite beauty and vibrant, bustling cities. Those without a bachelor’s degree can find limited opportunities to teach in Indonesia, but a four-year degree is preferred. TEFL certification is required. Most of those teaching English in Indonesia will find jobs in the major cities of Jakarta, Yogyakarta, Bandung, and Surabaya. There are teaching opportunities on the island of Bali; however, its popularity means the local job market is more competitive.
Westhill Consulting Career & Employment Australia agrees with the above blog but we would like to give a warning that some of these jobs are illegal. Be careful!
For more information:
http://westhillconsulting-career.com/
http://www.westhillconsulting-career.com/teaching.html
http://www.westhillconsulting-career.com/blog/

 Won't Start in Windows 7 with 2181
Won't Start in Windows 7 with 2181
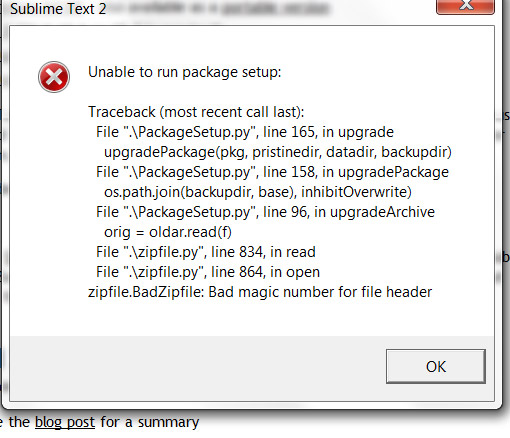

 Filename disappears from title when switching to fullscreen and back
Filename disappears from title when switching to fullscreen and back
Steps to reproduce:
1. Open file in Sublime Text 2
2. Change to Fullscreen view
3. Close Fullscreen view
4. Observe naked title bar
Seen in ST2 build 2023 on OS X 10.6

 The Avanti Law Group: Your Personal Lawyer
The Avanti Law Group: Your Personal Lawyer

Here is a law group that believes that the advice “Do not take your client’s case personally” is useless. Avanti Law Group goes to great lengths to give its clients the best results by taking each case as their own personal battle, getting involved in it by standing for the clients’ rights all the way through.

 No Support link in the Help menu option.
No Support link in the Help menu option.
Specs:
* Sublime Text 2.0.1
* Windows 7

 If first element of items array passed to show_quick_panel is an empty string, the program crashes when deleting a character from the input
If first element of items array passed to show_quick_panel is an empty string, the program crashes when deleting a character from the input
If show_quick_panel is called with an empty string as the first element of the items array argument, the program crashes when the the user deletes a character from their input.
Eg.
self.view.window().show_quick_panel(['', 'test1', 'test2'], self.on_done)

 Haskell syntax highlighting: comments in module declarations
Haskell syntax highlighting: comments in module declarations
Sublime doesn't recognize comments in the module declaration correctly:
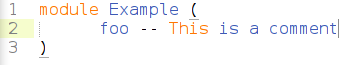
As far as I know, this behavior occurs only in the module declaration, and not in other (comment) places.

 [AppleScript ] Lines started with "#" are not being recognized as comments
[AppleScript ] Lines started with "#" are not being recognized as comments
You could read about AppleScript comments in the AppleScript Language Guide.
--
Same in the third version.

 Create a better color palette for windows. The plugin you"ll currently provide has a poor interface. Put something like the color palette on photoshop
Create a better color palette for windows. The plugin you"ll currently provide has a poor interface. Put something like the color palette on photoshop
Create a better color palette for windows. The plugin you"ll currently provide has a poor interface(standard windows color palette). Put something like the color palette on photoshop into sublime

 Leave goto anything open after selecting a file, so multiple files can be selected
Leave goto anything open after selecting a file, so multiple files can be selected

 Unsaved files
Unsaved files
If you create a new plain-text file, its first line becomes the displayed name for its tab or sidebar item. How can I disable this?
Customer support service by UserEcho

